This chapter describes how external parties can notify us of any security flaws in the Adyen mobile payments solution, and how we resolve any externally or internally reported security flaws or vulnerabilities.
In this context, a flaw is an implementation defect that can lead to a vulnerability, and a vulnerability is an exploitable condition in the code that allows an attacker to attack.
Public security flaw reporting
Adyen has a Responsible disclosure policy that is published on the Adyen website. We encourage external parties to notify Adyen of any security flaws they discover in the Adyen mobile payments solutions before informing the outside world, so that we can first take action.
The reporting and resolution process for security flaws consists of the following main steps:
-
The external party sends an email to responsibledisclosure@adyen.com. This email must:
- Include details that enable Adyen to reproduce the issue.
- Include the external party’s contact details.
- Be encrypted using the Adyen public PGP key.
-
Within 72 hours, we send an acknowledgement of receipt to the external party.
-
We categorize the risk associated with the issue, and in our project management tool (YouTrack) create a ticket to keep track of the reported issue and its resolution.
-
Within three working days, we send a notification to the external party with an assessment of the discovered issue.
-
We start to resolve the issue in relation to its categorization, and keep the external party informed of the progress made.
-
We validate the issue has been resolved and distribute a security patch.
-
After the issue is resolved, we and the external party decide together if and how it should be made public.
Vulnerability management policy
As soon as we become aware of a security flaw or vulnerability identified by internal or external parties, we take the following steps:
-
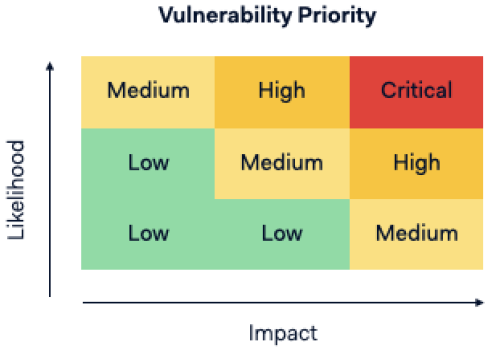
We rate the risk associated with the issue.
-
In our project management tool YouTrack, we create a ticket to keep track of the identified issue and its resolution.
We have a dedicated YouTrack project space for this type of tickets, called Vulnerability (VULN). The YouTrack ticket contains details about how to reproduce the issue and how to test that it has been resolved. -
Based on the risk level, we take action to resolve the issue and to validate that the issue has indeed been resolved.
-
We distribute a security patch to merchants.